OWASP Top 10: Cheat Sheet of Cheat Sheets
What Are OWASP Top 10 Cheat Sheets?
OWASP Top 10 Cheat Sheets are detailed resources providing practical guidance for the most critical security risks in web applications. Created by OWASP (Open Worldwide Application Security Project), they provide clear guidance on prevalent vulnerabilities for developers and security professionals. The current version of the OWASP cheat sheets reflects the latest revision of the OWASP Top 10 list from 2021.
By offering actionable advice, the OWASP Top 10 Cheat Sheet serves as a practical tool for implementing security measures. It covers areas such as exploitation techniques, secure coding practices, and mitigation strategies.
While the OWASP Cheat Sheets are an essential resource, they are a bit long and can take time to review. This is why we came up with a cheat sheet of cheat sheets—summarizing the cheat sheets for the top 10 OWASP vulnerabilities to give you quick actionable advice, with links to the full documents to learn more.
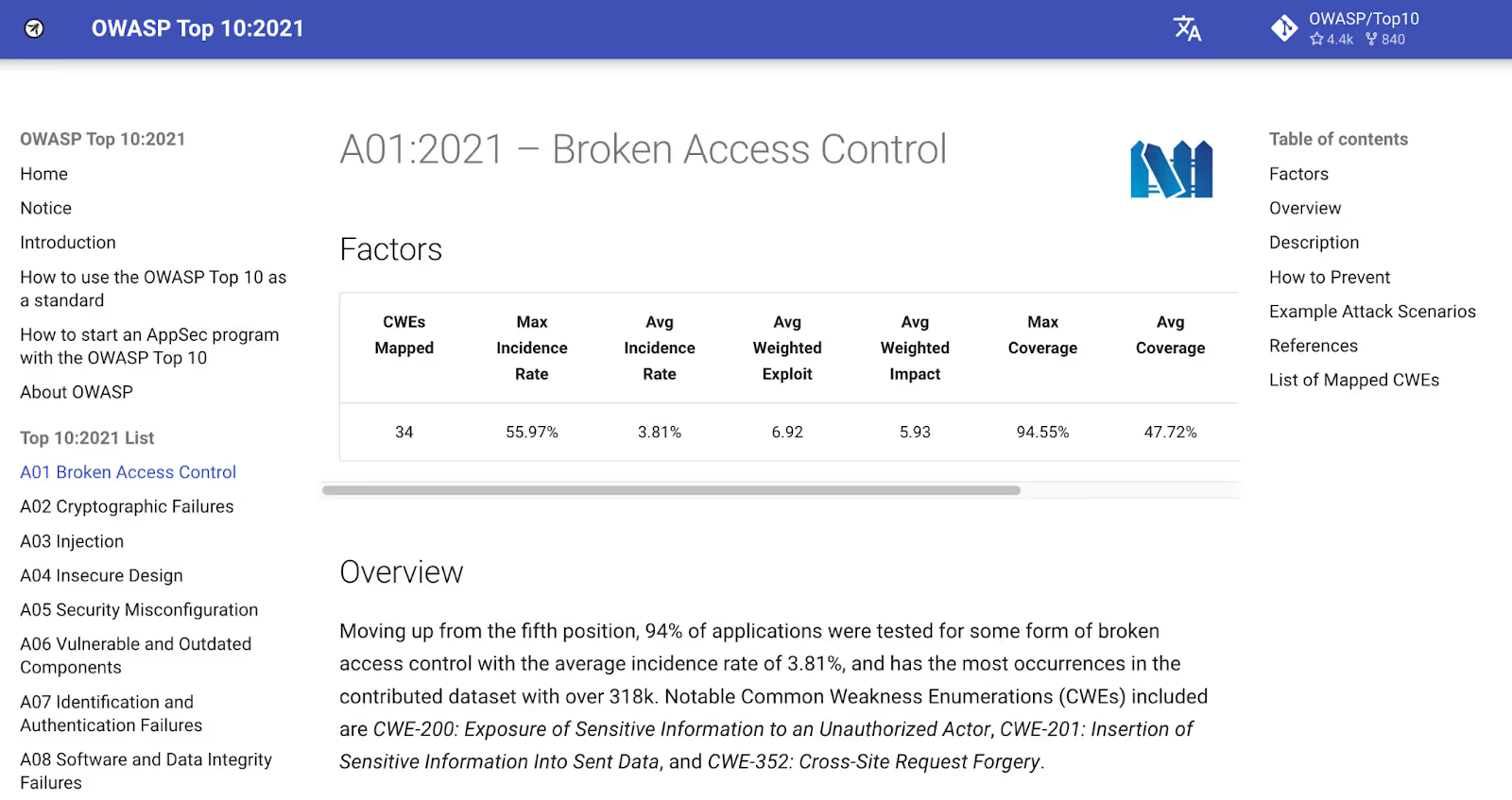
Below is the main page of the OWASP cheat sheet for A01:2021: Broken Access Control. You can access the full list of OWASP Top 10 cheat sheets here.
This is part of a series of articles about application security vulnerabilities.
OWASP Top Ten 2021 Cheat Sheet Summary
A01: Broken Access Control
Broken access control refers to vulnerabilities where attackers gain unauthorized access to restricted data or actions in a web application, often due to improper enforcement of user permissions. This can lead to unintended disclosure, modification, or deletion of data, and unauthorized use of application functionality.
Common examples of broken access control include:
- Privilege violations: Failing to enforce the principle of least privilege or a deny-by-default policy that allows broader access than intended.
- Parameter tampering and forced browsing: Attackers bypass access controls by altering URLs, parameters, or HTML pages, exploiting weaknesses to access restricted sections or manipulate API requests.
- Insecure direct object references (IDOR): Users access others’ accounts by providing an identifier, due to lack of proper ownership checks.
- Lack of access controls in APIs: Missing access control for actions like POST, PUT, and DELETE in APIs can allow unauthorized modification or deletion.
- Privilege escalation: Attackers act with elevated privileges, such as accessing admin functions while logged in as a standard user.
- JWT and cookie manipulation: Modifying JSON web tokens (JWTs), cookies, or hidden fields can lead to unauthorized access or privilege elevation.
- CORS misconfiguration: Misconfigured cross-origin resource sharing (CORS) allows access from unauthorized sources.
- Force browsing: Attackers access privileged or authenticated pages without proper authorization.
Best practices for preventing broken access control:
- Deny by default: Restrict access to all resources except explicitly-defined public ones.
- Centralized access control: Implement access control mechanisms in one place to ensure consistent checks across the application, and limit CORS usage where possible.
- Enforce ownership controls: Access controls should verify record ownership to prevent unauthorized CRUD (create, read, update, delete) actions.
- Business logic enforcement: Enforce unique business logic constraints within the application’s domain model, ensuring that users operate only within designated limits.
- Secure directory and metadata management: Disable directory listing on servers, and remove any sensitive metadata (e.g., backup files, .git) from web-accessible locations.
- Logging and monitoring: Log access control failures and alert administrators when necessary. Implement rate limiting on APIs and controllers to mitigate automated attacks.
- Session management: Invalidate session identifiers upon logout. For JWTs, use short expiration times to minimize exposure. For long-lived JWTs, follow OAuth standards to enable token revocation.
- Testing for access control: Conduct functional and integration testing for access control, ensuring each component enforces permissions correctly.
A02: Cryptographic Failures
Cryptographic failures occur when sensitive data is inadequately protected, particularly in transit or at rest, which exposes it to unauthorized access and potential misuse. This category of security vulnerabilities is critical for applications that handle sensitive information such as passwords, financial data, health records, and personal identifiers.
Weak encryption practices, improper key management, and outdated cryptographic methods all contribute to cryptographic failures.
Common examples of cryptographic failures include:
- Cleartext transmission: Transmitting data without encryption over protocols such as HTTP, FTP, or unprotected SMTP exposes it to interception, especially in untrusted networks.
- Weak or outdated cryptography: Using deprecated algorithms or weak protocols can make encrypted data vulnerable to attacks, as outdated methods (e.g., MD5, SHA-1) are easier to break.
- Inadequate key management: Failing to rotate keys, using default or weak keys, or embedding keys in source code compromises the security of encrypted data.
- Improper certificate validation: Neglecting to validate server certificates or trust chains can lead to man-in-the-middle (MITM) attacks.
- Insecure cryptographic practices: Reusing initialization vectors, choosing inappropriate cryptographic modes (e.g., ECB mode), and using non-cryptographic random functions for sensitive purposes can weaken encryption.
Best practices for preventing cryptographic failures:
- Data classification and minimal storage: Classify all processed, stored, or transmitted data based on sensitivity, following legal and regulatory standards. Avoid retaining sensitive data unless necessary, using tokenization or truncation where feasible.
- Encryption at rest and in transit: Encrypt sensitive data both at rest and in transit. Use TLS with forward secrecy, enforce encryption with HTTP strict transport security (HSTS), and avoid legacy protocols for sensitive data transmission.
- Up-to-date cryptographic standards: Use strong, modern algorithms and protocols with current key management practices. For passwords, employ adaptive, salted hashing functions (e.g., Argon2, bcrypt, or PBKDF2) with appropriate delay factors.
- Secure initialization vectors (IVs): Generate IVs with a cryptographically secure random generator when required by the cryptographic mode. Ensure IVs are unique for each encryption instance when using the same key.
- Authenticated encryption: Where feasible, use authenticated encryption rather than simple encryption to verify data integrity and authenticity.
- Avoid deprecated methods: Steer clear of obsolete cryptographic functions like MD5, SHA-1, and PKCS #1 v1.5 padding, and ensure no weak or exploitable padding schemes are in use.
- Independent security review: Regularly review cryptographic configurations, settings, and implementations to ensure effectiveness and compliance with security best practices.
A03: Injection
Injection attacks occur when untrusted data is inserted into an application in a way that it modifies the intended behavior of commands or queries, potentially allowing attackers to execute unauthorized commands or access sensitive data.
These attacks are often possible because of insufficient validation or sanitization of user inputs. Common types of injection attacks include SQL, NoSQL, OS command, LDAP, and expression language (EL) injections, each targeting specific interpreters or query languages.
Common examples of injection vulnerabilities include:
- Unvalidated input: Applications that don’t validate or sanitize user-supplied data are at risk, as malicious inputs can be executed as part of commands.
- Dynamic queries without parameterization: Using dynamic queries or concatenating user input directly into SQL statements without parameterized queries or context-aware escaping makes injection attacks more feasible.
- Object relational mapping (ORM) vulnerabilities: ORMs that process untrusted inputs can be exploited to retrieve or manipulate additional, sensitive records.
- Direct concatenation in commands: Directly embedding hostile data within commands or stored procedures can lead to unintended command execution, exposing the application to attackers.
Best practices for preventing injection attacks:
- Use safe APIs: Avoid direct interpreter use by utilizing safe APIs or parameterized interfaces. For database operations, use ORMs or parameterized queries. Note that parameterized stored procedures can still be vulnerable if they concatenate commands and data within dynamic SQL functions like EXECUTE IMMEDIATE or exec().
- Server-side input validation: Validate all inputs on the server side using positive validation (e.g., allowing only known safe characters). While not foolproof, input validation is an important layer of defense.
- Escape special characters: For any necessary dynamic queries, apply context-specific escaping to special characters. However, structure elements like table names and column names cannot be safely escaped, so avoid using user input for database structure components.
- Limit query results: Use SQL controls such as LIMIT to reduce the impact of successful injection attempts, preventing excessive data exposure.
A04: Insecure Design
Insecure design refers to the absence or ineffectiveness of security controls in the architecture or design phase of software development, leading to vulnerabilities that cannot be mitigated by subsequent implementation fixes.
Unlike insecure implementations, which arise from coding errors, insecure design issues stem from an inadequate consideration of security needs during the planning stages, leaving the application vulnerable by design. Such flaws are often due to a lack of risk assessment or failure to consider necessary security controls for protecting data.
Common examples of insecure design include:
- Lack of business risk profiling: Without an assessment of the business risks, applications may be built with insufficient security measures, failing to align with the sensitivity of the data or operational impact.
- Insufficient security requirements: If security requirements are not well-defined and integrated into the technical specifications, the system may lack essential defenses.
- Poor requirement management: Inadequate gathering and management of requirements, particularly around data confidentiality, integrity, and access control, can lead to gaps in the security design.
- Missing threat modeling: Failing to evaluate and address potential threats at the design level leaves vulnerabilities open to exploitation.
Best practices for preventing insecure design:
- Adopt a secure development lifecycle (SDLC): Incorporate security processes throughout the development lifecycle, collaborating with application security (AppSec) professionals to design appropriate security and privacy controls.
- Implement secure design patterns: Use a library of secure design patterns and pre-approved, secure components to streamline the development of secure applications.
- Conduct threat modeling: Apply threat modeling for critical application components, especially for authentication, access control, and business logic. This helps identify and mitigate potential risks early in the design process.
- Integrate security into user stories: Embed security controls and assumptions directly within user stories to ensure that security requirements are addressed from the beginning.
- Validate assumptions through testing: Develop and execute unit and integration tests that validate critical flows against the threat model, checking that assumptions hold under various scenarios.
- Establish layer segregation: Design with segregation at both the system and network layers, adjusting protection based on exposure and security needs, and segregate tenant data as necessary.
- Limit resource usage: Implement resource controls to restrict the amount of processing or data each user or service can consume, mitigating the impact of potential misuse.
A05: Security Misconfigurations
Security misconfigurations arise when applications and systems are deployed with inadequate security settings, leading to vulnerabilities that can be easily exploited. This is one of the most common security issues, occurring when security settings are incomplete, inconsistent, or absent across application components, frameworks, or infrastructure.
Common indicators of security misconfigurations include:
- Unsecured application stack: Missing security hardening or misconfigured permissions across any layer, including databases, cloud services, and network settings, creates vulnerabilities.
- Enabled unnecessary features: Enabling unneeded ports, services, or accounts increases the attack surface.
- Default accounts and credentials: Retaining default accounts and unchanged passwords poses a major security risk, allowing attackers easy access.
- Excessive error information: Stack traces and detailed error messages displayed to users can inadvertently reveal sensitive information about the application.
- Unconfigured or disabled security features: Applications that have been upgraded may lack the latest security configurations, particularly if new features aren’t enabled.
- Insecure application settings: Servers, frameworks, libraries, and databases with permissive or insecure default configurations are vulnerable to attack.
- Outdated components: Using outdated software components introduces additional security flaws (also related to the risk of vulnerable and outdated components).
Best practices for mitigating security misconfigurations:
- Implement repeatable hardening processes: Use a consistent hardening process for all environments to ensure each one (development, QA, production) is configured securely. This should be automated where possible to minimize setup time and reduce human error. Use different credentials for each environment.
- Deploy a minimal platform: Install only necessary features, components, and frameworks. Remove or disable any unused functionality, documentation, and sample files.
- Routine configuration review and patch management: Regularly review and update configurations to align with security advisories and patches. This includes reviewing cloud storage permissions and adhering to best practices for cloud security (e.g., securing S3 buckets).
- Architecture segmentation: Use network segmentation, containerization, or cloud security groups (ACLs) to isolate application components and tenants, enhancing security between different parts of the application.
- Enforce security headers: Set and verify security headers, such as content security policy (CSP) and HTTP strict transport security (HSTS), to protect clients from various attacks.
- Automated configuration validation: Use automated tools to regularly check that configurations meet security standards across all environments, ensuring settings are effective and consistently applied.
A06: Vulnerable and Outdated Components
Vulnerable and outdated components pose significant risks to applications because they may contain unpatched security flaws, creating opportunities for attackers to exploit these weaknesses. Many applications depend on third-party libraries, frameworks, and other components, making it essential to manage and update these dependencies continuously.
Common indicators that an application may be vulnerable due to outdated components:
- Lack of component inventory: Without a comprehensive inventory of component versions, including nested dependencies, it’s challenging to track and manage potential vulnerabilities.
- Unpatched or outdated software: Components such as the OS, application servers, APIs, runtime environments, and libraries should be maintained with the latest security patches. Unsupported or outdated software is particularly susceptible to attack.
- Absence of regular vulnerability scanning: Failing to regularly scan for vulnerabilities and monitor security bulletins increases the risk of unaddressed issues.
- Delayed patch application: Relying on infrequent patching cycles (e.g., monthly or quarterly) can leave components unprotected for extended periods, increasing exposure to known vulnerabilities.
- Compatibility issues with updates: Developers who do not test updated libraries for compatibility may avoid or delay necessary updates, perpetuating vulnerability risks.
- Unsecured component configurations: Neglecting to secure configurations of components (related to security misconfiguration) further heightens the risk.
Best practices for addressing vulnerable and outdated components:
- Maintain a continuous inventory: Use tools like OWASP Dependency Check, retire.js, or software composition analysis (SCA) tools to track the versions of all components (client-side and server-side) and their dependencies. Regularly monitor sources like the Common Vulnerabilities and Exposures (CVE) database and the National Vulnerability Database (NVD) for updates on component vulnerabilities.
- Automate vulnerability scanning and monitoring: Implement automated scanning tools to monitor component vulnerabilities consistently. Subscribe to security alerts relevant to the components to stay informed of new risks.
- Use secure sources and signed packages: Only download components from official, secure sources, and prefer signed packages to ensure that components have not been tampered with.
- Address unmaintained libraries: Regularly evaluate libraries and components for active maintenance and security patches. For unmaintained components, consider virtual patching solutions that can detect and protect against known vulnerabilities.
- Plan for ongoing updates: Establish an ongoing process to monitor, prioritize, and apply updates, patches, and configuration changes for the entire application lifecycle, ensuring continuous risk mitigation.
A07: Identification and Authentication Failures
Identification and authentication failures occur when applications lack strong mechanisms to confirm user identities and manage sessions securely. This category includes vulnerabilities that allow attackers to compromise user accounts, exploit weak session handling, or bypass authentication protocols altogether, leading to unauthorized access.
Common examples of authentication vulnerabilities include:
- Exposure to automated attacks: Systems that allow repeated login attempts without sufficient rate limiting or multi-factor authentication (MFA) are susceptible to attacks like credential stuffing, where attackers use automated scripts with known usernames and passwords.
- Weak password policies: Accepting default, predictable, or easily guessed passwords (e.g., "admin/admin" or "Password123") leaves accounts open to brute force attacks.
- Insecure password storage: Storing passwords in plaintext or using weak hashing methods can expose sensitive data if breached (related to cryptographic failures).
- Insufficient MFA: MFA significantly reduces the risk of unauthorized access, and its absence makes accounts vulnerable to credential-based attacks.
- Inadequate session management: Exposing session identifiers in URLs or failing to regenerate session IDs after login increases the risk of session hijacking. Failing to invalidate sessions correctly upon logout or inactivity also leaves sessions susceptible to misuse.
Best practices for preventing identification and authentication vulnerabilities:
- MFA: Use MFA wherever possible, especially for sensitive accounts, to protect against credential stuffing, brute force, and reuse of stolen credentials.
- Avoid default credentials: Remove any default credentials from deployed applications, particularly for administrative accounts, to prevent unauthorized access.
- Enforce strong password policies: Use a password policy aligned with modern standards, such as NIST 800-63b, which recommends longer, memorable passwords over complex but short passwords. Check new passwords against commonly used password lists to prevent weak passwords.
- Protect credential recovery processes: Harden registration, password recovery, and API paths against account enumeration by standardizing error messages across success and failure scenarios.
- Rate-limit failed logins: Set limits on login attempts or apply delays after repeated failures to slow down brute force attempts without causing denial-of-service issues. Log and monitor unusual login failures to detect credential stuffing or brute force attempts.
- Use secure session management: Implement a server-side session manager that generates a new, high-entropy session ID after login. Session identifiers should be kept out of URLs, stored securely, and invalidated on logout, after a period of inactivity, or when the session expires.
A08: Software and Data Integrity Failures
Software and data integrity failures occur when applications lack mechanisms to ensure the trustworthiness of code, dependencies, and data. This category includes risks related to untrusted sources, unsecured build and deployment processes, and the absence of integrity checks for auto-updates, plugins, and dependencies.
Without strong integrity controls, applications become susceptible to attacks, such as dependency confusion, supply chain compromises, and insecure deserialization, allowing attackers to introduce malicious code or tampered data into production environments.
Common examples of integrity failures include:
- Reliance on untrusted sources: Using plugins, libraries, or modules from unverified sources or external repositories, such as public npm or Maven repositories, increases the risk of injecting malicious code.
- Insecure CI/CD pipelines: Poorly secured CI/CD pipelines can be exploited to insert unauthorized changes or introduce malware into the build process, potentially affecting all downstream deployments.
- Unsafe auto-update mechanisms: Applications that use auto-update functionality without verifying update integrity are vulnerable to supply chain attacks, where attackers could push malicious updates.
- Insecure serialization: Sending serialized data to untrusted clients without integrity checks or digital signatures enables attackers to manipulate or replay data, potentially compromising application behavior and security.
Best practices for preventing software and data integrity failures:
- Verify software integrity: Use digital signatures or similar verification mechanisms to confirm that software and data originate from trusted sources and have not been tampered with. This applies to all dependencies, updates, and third-party components.
- Use trusted repositories: Limit dependency downloads to trusted repositories. For higher security, consider hosting an internal repository that has been thoroughly vetted to ensure known-good versions of libraries and dependencies are used.
- Employ software supply chain security tools: Utilize tools like OWASP Dependency Check or OWASP CycloneDX to scan and verify dependencies, identifying known vulnerabilities and preventing their inclusion in the software.
- Establish a rigorous review process: Implement a code and configuration review process within the development pipeline to minimize the risk of introducing malicious or unauthorized changes.
- Secure CI/CD pipelines: Ensure that CI/CD pipelines have strict access control, configuration management, and segregation to protect code integrity throughout the build and deployment processes.
- Protect serialized data: Avoid sending unsigned or unencrypted serialized data to untrusted clients. Where serialized data must be exposed, apply digital signatures or integrity checks to detect tampering or replay attempts.
A09: Security Logging and Monitoring Failures
Security logging and monitoring failures occur when applications lack adequate mechanisms to detect, respond to, and investigate potential security breaches. Without sufficient logging and monitoring, malicious activities may go unnoticed, delaying incident response and allowing attacks to persist undetected.
This category includes failures to log critical events, insufficient or unclear log messages, and ineffective alerting and monitoring, all of which hinder the ability to respond to active threats.
Common examples of logging and monitoring failures include:
- Missing or inadequate logging: Important events, such as user logins, failed login attempts, and high-value transactions, are not logged or are logged without essential context, making it difficult to trace suspicious activities.
- Unmonitored logs: If application and API logs are not routinely monitored, potential indicators of compromise (IoCs) or malicious behavior may be missed.
- Local-only log storage: Storing logs solely on local systems increases the risk of data loss and makes centralized monitoring challenging.
- Lack of alerts for suspicious activity: Without well-defined alert thresholds or escalation processes, organizations may fail to respond to active attacks in real time.
- Insufficient incident response capabilities: Applications that cannot detect, escalate, or alert for active attacks in a timely manner leave organizations unprepared for rapid response.
- Information leakage through logs: Logs that reveal too much information to users or attackers can inadvertently expose security details and increase risk.
Best practices for addressing security logging and monitoring failures:
- Log critical events with sufficient context: Ensure that all authentication, access control, and input validation failures are logged with enough user and system context to identify potential malicious actions. Retain logs for sufficient time to support delayed forensic analysis if needed.
- Standardize log formats: Use a standardized log format compatible with log management and analysis solutions to facilitate easier monitoring and investigation.
- Secure log data: Encode log data properly to prevent injection attacks that could compromise logging and monitoring systems.
- Audit trails for high-value transactions: Establish an audit trail for sensitive actions, using tamper-resistant methods like append-only database tables to maintain data integrity and support forensic analysis.
- Set up effective monitoring and alerting: DevSecOps teams should deploy monitoring and alerting systems to detect suspicious behavior promptly. Tools like the Elasticsearch, Logstash, Kibana (ELK) stack can be used to build custom dashboards and alerts.
- Develop an incident response plan: Establish and regularly update an incident response and recovery plan, following frameworks such as NIST 800-61r2, to ensure a structured approach to handling detected security events.
- Use application protection tools: Consider using commercial or open-source security frameworks like the OWASP ModSecurity Core Rule Set to provide additional application protection, correlating logs and detecting potential security events.
A10: Server-Side Request Forgery (SSRF)
Server-Side Request Forgery (SSRF) vulnerabilities occur when a web application allows user input to control requests to external or internal resources without proper validation. This enables attackers to craft malicious requests that the server executes, potentially accessing sensitive data or internal services not normally exposed to the internet.
SSRF attacks can bypass firewalls, VPNs, and other network controls, making them particularly dangerous in complex, cloud-based architectures where internal services may be accessible only from within specific network zones. The increase in SSRF incidents is attributed to web applications frequently needing to fetch URLs as part of their functionality.
Common examples of SSRF vulnerabilities include:
- Open URL fetching: Allowing user input to dictate external or internal resource requests without validating or sanitizing the URL.
- Default trust: Applications that implicitly trust user-supplied URLs and forward them without restriction.
- Blind SSRF: Scenarios where attackers exploit SSRF to interact with internal systems without seeing the responses but infer outcomes from side effects (e.g., response times, errors).
- File protocol exploitation: Exploiting non-HTTP protocols (like file://) when such protocols are improperly supported by the server.
- DNS rebinding: Manipulating the DNS resolution of allowed domains to point to sensitive internal systems.
- Accessing cloud metadata services: Targeting cloud environments by requesting sensitive metadata endpoints (e.g., AWS EC2 metadata service) via SSRF.
Best practices for preventing SSRF:
- Network segmentation: Isolate any functionality that requires remote resource access onto separate network segments, limiting SSRF impact if exploited.
- “Deny by Default” firewall policies: Apply firewall and network access control rules that block all internal and sensitive network traffic except for explicitly allowed endpoints. Ensure that all traffic to these endpoints is logged for monitoring and auditing purposes, aligning with logging and monitoring best practices.
- Strict input validation: Validate and sanitize all URLs provided by clients to ensure only trusted destinations are reachable.
- Allow-list URL enforcement: Enforce a strict allow list for permitted URL schemas, ports, and destinations, preventing requests to unauthorized locations.
- Disable HTTP redirections: Avoid redirects within HTTP responses to prevent attackers from redirecting SSRF requests to unintended locations.
- Avoid raw responses: Do not return raw server responses to clients, as these may leak sensitive information.
- Handle URL consistency: Be cautious of URL parsing and handling issues like DNS rebinding or "time of check, time of use" (TOCTOU) race conditions, which can be manipulated to bypass SSRF protections.
- Avoid critical services on front systems: Don’t deploy critical services, such as authentication systems (e.g., OpenID), on systems that may receive user-controlled input to reduce risk from SSRF attacks.
- Implement network encryption: Use network encryption protocols like VPNs for frontends with specific, trusted user groups, particularly when higher protection levels are needed.
5 Main Security Takeaways from OWASP Cheat Sheet Guidelines
The following are common takeaways for developers and security teams from all the OWASP cheat sheet recommendations:
- Enforce least privilege and deny by default: Restrict user and system access to the minimal set of resources and actions necessary for functionality. Default settings should deny access unless explicitly permitted, and sensitive actions must validate ownership or authorization.
- Secure data with encryption at all stages: Protect sensitive data both at rest and in transit using strong encryption standards. Use adaptive hashing methods (e.g., Argon2, bcrypt) for password storage and enforce secure transport protocols like TLS with HSTS.
- Maintain and monitor component integrity: Regularly update all software components, dependencies, and libraries to address vulnerabilities. Use automated tools for continuous monitoring and ensure components come from trusted sources. Secure CI/CD pipelines to protect the integrity of builds and deployments.
- Implement multi-layered input validation: Validate and sanitize all user inputs on the server side to prevent injection attacks, SSRF, and other vulnerabilities. Employ allow lists for URLs, enforce parameterized queries, and use input validation as a defense-in-depth strategy alongside secure coding practices.
- Develop strong logging, monitoring, and incident response plans: Log critical security events, standardize log formats, and ensure logs are securely stored and monitored. Use tools for real-time alerting and analysis, and maintain an up-to-date incident response plan to detect and mitigate breaches quickly.
Related content: Read our guide to OWASP top 10 LLM.
Defending Against OWASP Top 10 Threats with Oligo
Oligo Security delivers real-time threat detection and prioritized vulnerability management to help organizations defend against the OWASP Top 10 vulnerabilities. By combining runtime monitoring with contextual insights, Oligo enables faster identification and mitigation of risks without compromising performance.
Key Capabilities with Oligo
- Runtime Threat Detection: Monitors application behavior to identify unauthorized access, injection attempts, and misconfigurations.
- Vulnerability Prioritization: Focuses on exploitable vulnerabilities with Oligo Focus, ensuring teams address the highest-risk issues first.
- Access Control and API Protection: Enforces rules to prevent privilege escalation and API misuse.
- Secure Input and Output Handling: Validates inputs and sanitizes outputs to block injection attacks and data exposure.
- Continuous Monitoring: Provides actionable insights and compliance reporting to support ongoing security improvements.
Addressing OWASP Top 10 Threats
- Broken Access Control: Ensures least-privilege enforcement and ownership validation to prevent unauthorized access.
- Cryptographic Failures: Implements modern encryption standards and monitors key management practices.
- Injection Attacks: Detects and blocks malicious inputs using real-time filtering and rule enforcement.
- Insecure Design: Validates application logic and workflows during runtime, reducing design-level risks.
- Vulnerable Components: Tracks dependencies and flags outdated or insecure libraries for remediation.
Why Oligo?
Oligo’s solutions, ADR and Focus, provide real-time insights and exploitability analysis to defend against OWASP vulnerabilities. With automated prioritization and proactive defenses, Oligo simplifies vulnerability management and strengthens application security.
Secure your applications against OWASP vulnerabilities — schedule a demo today.
expert tips
Subscribe and get the latest security updates
Built to Defend Modern & Legacy apps
Oligo deploys in minutes for modern cloud apps built on K8s or older apps hosted on-prem.

