CVE-2025-61882: Oracle E-Business Suite Zero-Day Exploited in Clop Extortion Campaigns

TL;DR
- Critical unauthenticated remote code execution (RCE) in Oracle E-Business Suite (EBS)
- Actively exploited in Clop-led data theft and extortion attacks
- Exploit and Oracle source code leaked publicly
- Emergency patch released
Oracle has released an emergency patch for a critical zero-day vulnerability in Oracle E-Business Suite, tracked as CVE-2025-61882. The flaw, with a CVSS score of 9.8, allows attackers to execute arbitrary code remotely without authentication.
Reports from Oracle, Mandiant, and independent researchers confirm the vulnerability has been actively exploited in Clop ransomware group campaigns, leading to large-scale data theft and extortion. Public indicators of compromise (IOCs) now match exploit code that leaked on Telegram, confirming this is the same vulnerability used in recent attacks.
The timeline
- June 2025: Dark Web posts advertise an Oracle EBS zero-day exploit for sale (~$70,000).
- August 2025: Clop begins an extortion campaign targeting EBS servers across multiple organizations.
- October 4, 2025: Oracle publishes a Security Alert for CVE-2025-61882 and releases an emergency patch.
- October 5, 2025: Mandiant confirms Clop leveraged both previously patched July vulnerabilities and this new zero-day.
- October 6, 2025: Exploit archive and partial Oracle source code leaked by a group calling itself Scattered Lapsus$ Hunters.
How the Exploit Works
The vulnerability lies in the BI Publisher Integration component of Oracle’s Concurrent Processing module, part of EBS versions 12.2.3 through 12.2.14. It allows unauthenticated attackers to send specially crafted HTTP requests that lead to remote code execution on the affected server.
While Oracle’s advisory doesn’t specify the root cause, analysis of the leaked exploit shows that attackers used a server-side request forgery (SSRF) vector to force vulnerable systems to download and execute attacker-controlled code. Once code execution is achieved, the attackers gain full control of the EBS host, allowing them to exfiltrate sensitive ERP data and open a reverse shell for ongoing access.
Public IOCs uncovered by Oracle can be viewed in their advisory.
This pattern is consistent with Clop’s broader history of exploiting enterprise-grade application zero-days for extortion, including MOVEit Transfer, GoAnywhere MFT, and SolarWinds Serv-U.
Application-Layer Exploits Move Fast
Modern data theft campaigns are no longer about phishing or malware delivery. They begin directly in the application layer. Once a flaw like this becomes public, exploitation follows within hours.
In this case, the exploit appeared for sale months before patch availability, giving threat actors ample lead time. By the time the patch dropped, active exploitation was already confirmed, with multiple victims reporting ransom emails claiming stolen data from their Oracle EBS environments.
These attacks highlight the widening visibility gap between endpoint-focused defenses and application-layer attacks. Traditional tools such as EDR or CWPP can detect post-exploitation activity, but they don’t observe the initial exploit or code execution within the app’s process — where the breach actually begins.
Blending In with Legitimate Behavior
One reason these exploits evade early detection is how quietly they operate, as the attacker can control the exploit payload and the post-exploitation activity to bypass and avoid detection.
After exploiting the flaw, attackers didn’t deploy custom malware or implants. Instead, they used native system utilities and simple shell commands to move laterally and exfiltrate data -- the same “living-off-the-land” approach we’ve seen in prior campaigns.
From a system’s perspective, it’s just another Java process starting a process. Without application context, these look like routine operations. This is exactly where runtime visibility becomes crucial.
Why Cloud Application Detection & Response (CADR) Matters
Exploits like CVE-2025-61882 show why organizations can’t rely solely on traditional security telemetry and detection tools to catch application-layer threats. The initial compromise happens at runtime, often invisible to legacy monitoring.
With Cloud Application Detection & Response (CADR), defenders can monitor runtime behavior in real time, linking suspicious actions, like a Java process spawning a shell, directly to application activity.
Oligo CADR detects the root cause at runtime, not just downstream symptoms. Deep Application Inspection (DAI) surfaces rich, software-aware signals and correlates each event to a precise execution context, revealing exploitation techniques as they happen — and tying them back to the exact code path and component. That means it exposes intent, not just outcome.
For example, Oligo CADR detects XSLT injection techniques used to achieve remote code execution in Oracle EBS BI Publisher. The detection is payload-agnostic and focuses on the exploitation technique itself, generalizing to future variants even as payloads evolve.
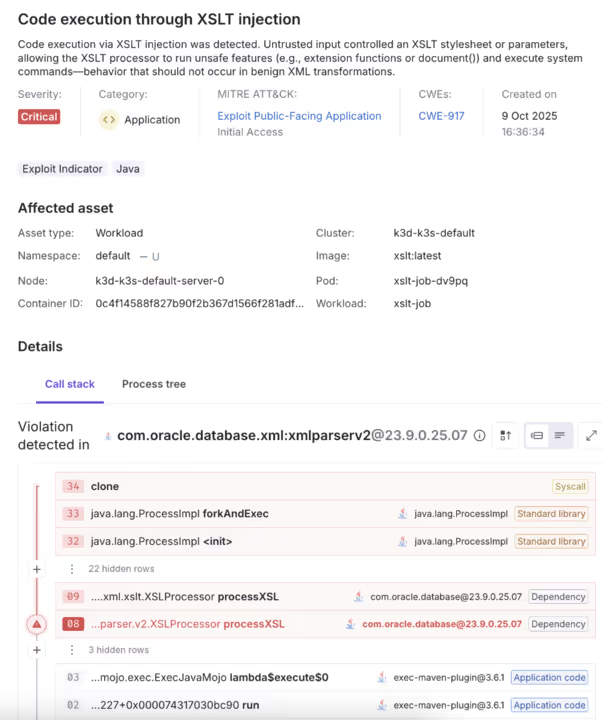
Overall, this is a perfect example of the third-party risk management capabilities that CADR provides. Oracle E-Business Suite is a fully third-party application running inside customer environments — Oracle customers don’t own the code or control how it’s built, yet they bear responsibility for securing it once it’s deployed.
What makes CADR so powerful is its ability to identify attacks like this inside vendor-supplied, first-party code — not because a CVE exists, but because of the exploit’s behavior at runtime. By anchoring detection to execution patterns rather than static payloads, CADR reveals exploitation as it unfolds, giving defenders visibility and protection where it matters most: at runtime.
Recommended actions
- Patch immediately: Apply Oracle’s Security Alert update for CVE-2025-61882. Ensure the October 2025 Critical Patch Update is installed first.
- Hunt for the following IOCs: Reverse shell commands (/bin/bash -i >& /dev/tcp), unexpected child processes from the EBS Java service, the IPs 200.107.207.26 and 185.181.60.11, and presence of files exp.py, server.py, or oracle_ebs_nday_exploit*.zip.
- Review access exposure: Identify any externally accessible EBS instances or outdated versions.
- Increase runtime visibility: Monitor for process and library behavior within application workloads, not just endpoints.
Runtime as the new battleground
CVE-2025-61882 is another reminder that the front line of today’s attack surface is runtime. Exploits like this one move fast, bypass traditional security boundaries, and rely on stealth more than noise.
As attackers increasingly weaponize vulnerabilities in enterprise software, organizations must evolve detection to the runtime itself, where exploitation begins. Waiting for downstream alerts is no longer enough. Detecting the first command execution inside the application is how modern defenders can get ahead and stay ahead.
.svg)




