Why KEV Changes the Conversation
For years, security teams relied on “Top CWE” and “Top CVE” lists to prioritize their efforts. These rankings, often rooted in theoretical severity or perceived impact, helped organizations make sense of an overwhelming vulnerability landscape. But the launch of CISA’s Known Exploited Vulnerabilities (KEV) catalog in 2021 changed the game.
The KEV catalog doesn’t just highlight vulnerabilities that could be dangerous; it tracks those that are actively being exploited in the wild. This subtle but powerful shift reframed how defenders think about prioritization. Instead of playing a numbers game with thousands of possible vulnerabilities, organizations could focus their energy on the weaknesses that adversaries actively target.
Oligo’s approach to runtime security is designed with this shift in mind: to help teams detect and mitigate the weaknesses that matter most, with greater precision and coverage than conventional solutions.
The CWEs Attackers Actually Exploit
When CISA analyzed the KEV catalog for 2024, a clear pattern emerged: attackers don’t scatter their efforts evenly across all vulnerability classes. Instead, they cluster around a relatively small group of Common Weakness Enumerations (CWEs) that consistently allow them to be successful and have the highest impact.
Here are the top CWEs identified in the KEV catalog:
What’s striking is that these CWEs are not always the ones that dominate the headlines or training exercises. For example, while Cross-Site Scripting (XSS) is often cited as a top CWE in general rankings, it is less frequently represented in KEV because adversaries have found other classes (like injection or memory corruption flaws) to deliver more high-value results in targeted attacks.
Why are attackers leveraging these vulnerabilities? They often have a higher impact, leading to privilege escalation, remote code execution (RCE), control, and persistence.
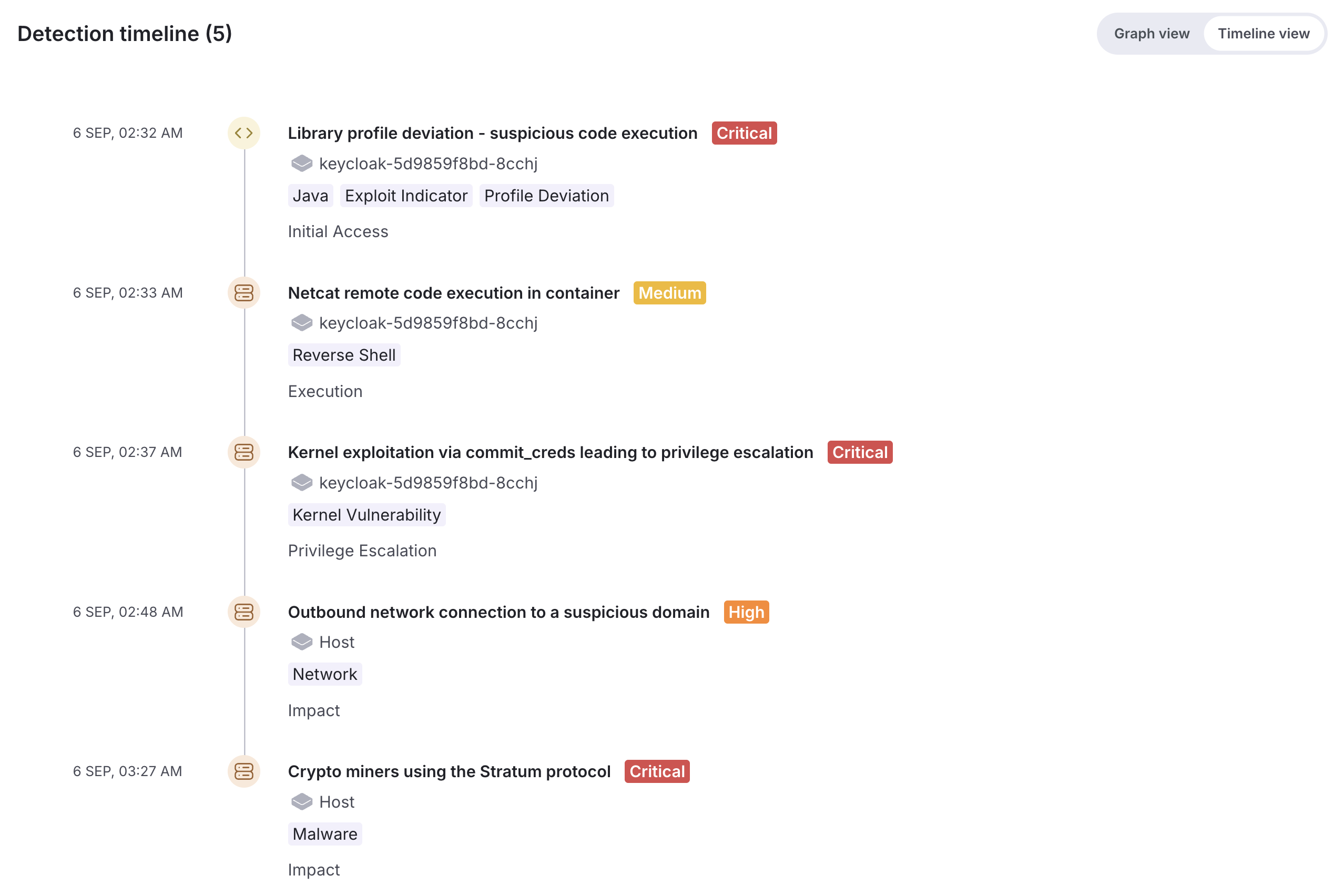
Similarly, type confusion vulnerabilities were the second most common type of exploited vulnerability, yet these threats didn’t even rank on the CWE top 25 list. Type confusion ranks low because CWE scoring is driven by frequency across all software categories. It ranks high in exploitation reports because attackers disproportionately target it in browsers and JIT engines, where it yields reliable (and impactful) RCE.
For defenders, this means realignment is essential. A vulnerability program focused only on generic “Top 25 CWEs” is likely to waste cycles on issues that attackers rarely exploit, while leaving gaps in the areas that matter most.
Why Conventional Detection Falls Short
Despite the clarity that KEV brings, most security tools and practices haven’t kept pace. The issue isn’t simply about CWE or CVE reporting—it’s about the approach to detection itself.
Most traditional security tools (SCA, CWPP, EDR, WAF, API security) were designed to detect symptoms of attacks—not the actual exploitation.
- Static Detection Creates Noise
Many tools rely heavily on static analysis, which flags potential weaknesses without indicating whether they can actually be exploited in a running application. This produces overwhelming volumes of alerts, erodes developer trust, and often leaves critical issues unresolved because teams can’t separate signal from noise. - Catching Symptoms, Not Root Exploits
Other solutions focus on downstream symptoms of a successful attack rather than the initial attack vector where the exploitation occured. The challenge is that symptoms can be easily manipulated by an attacker to bypass detection. For example, attackers can manipulate traces and payloads that may appear as legit
For example, they may detect suspicious system behavior after the fact, but fail to identify the root exploitation such as command injection (CWE-78), code injection (CWE-94), or other types of remote code execution (RCE) at the moment it happens. This lack of visibility creates confusion and leaves SOC and cloud security teams in the dark until an attacker makes their next move beyond the initial exploit attempt.
The result: organizations face both alert fatigue and a dangerous lack of clarity. Developers don’t know which vulnerabilities to prioritize, while defenders risk overlooking active exploitation until it’s too late.
Oligo’s Approach: Precision, Coverage, and Context
Oligo was built to address this gap. Unlike legacy tools that prioritize breadth over depth, Oligo’s detection strategy is designed to deliver better correlation with visibility into both an application’s running code and infrastructure.
1. Comprehensive Coverage Across High-Impact CWEs
Oligo’s coverage spans the KEV-prioritized CWEs, including memory management flaws like CWE-787 and CWE-416, which are notoriously difficult for static and traditional analysis tools to catch since they focus on CVEs and payloads. Oligo’s behavioral detection techniques analyze runtime patterns to catch exploitation attempts that would otherwise slip by other tools.
2. Context-Aware Insights
Detection without context creates noise. Oligo integrates environmental context—cloud workload configurations, application workflows, and runtime dependencies—to create complete pictures of incidents that identify the root cause that needs to be fixed, drastically decreasing mean-time-to-resolution (MTTR). This ensures that when a deserialization flaw (CWE-502) is flagged, teams know whether it’s exploitable in their actual deployment, not just in theory.
3. Seamless Integration for Modern Teams
CISOs need assurance that investments tie to ROI, while engineers need tools that don’t block development. Oligo’s platform is designed to run without any CI/CD integration or access to source code management systems. For cloud security engineers and SOC teams, runtime insights reduce false positives and ensure that performance and stability won’t be compromised.
To Protect Against Common Threats, Start at Runtime
CISA’s KEV catalog has made one thing clear: not all vulnerabilities are created equal. Attackers consistently exploit a relatively small set of CWEs, and defending effectively means zeroing in on those weaknesses with precision and context that only exists at runtime.
Traditional tools weren’t designed with this in mind. They report broadly, often without aligning to the risks that matter most. Oligo changes that dynamic by delivering high-fidelity, KEV-aligned detection that deploys easily into cloud environments.
By focusing where attackers focus, Oligo helps organizations transform their vulnerability management and threat detection and response from a numbers game into a targeted, ROI-driven defense strategy—ensuring security teams are always one step ahead of real-world threats.

.png)
.png)